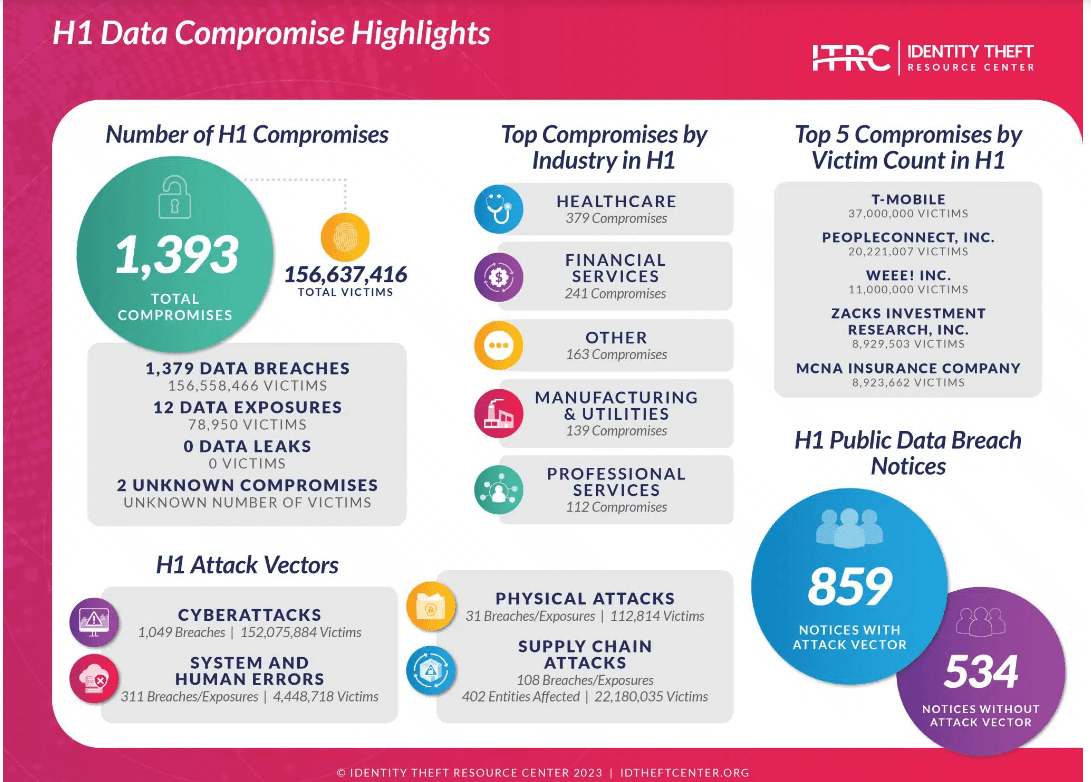
Data Breach Stats and the SEC’s New Rule

Right image – IBM’s annual Cost of a Data Breach Report, reveals that the global average cost of a data breach reached 4.45 Million, an all-time high for the 18 year old report. The comprehensive analysis by the Ponemon Institute covers 553 organizations with actual data breaches. Click the image for more highlights from the report including the impact of AI and involving law enforcement.
SEC Rule
On July 26th, the Securities and Exchange Commission (SEC) adopted new rules that require public companies to disclose significant cybersecurity incidents within 4 days. You may have seen this on our LinkedIn page last week.
Brandon Quinn, a lawyer and technologist says, “These new cybersecurity incident reporting rules are set to take effect in December. However, smaller companies will be granted an additional 180 days before they are required to provide Form 8-K disclosures.
…This reporting requirement will no doubt for consistency spread in the coming years to other stock exchanges due to the financial and reputational impact of substandard Cybersecurity controls.
This will certainly raise Cybersecurity and Data Protection importance in the board room in budgeting decisions due to the potential liability of the board for any inaccurate disclosures.”
Why does all this matter to you?
The number of breaches continues to increase. The cost of identifying, mitigating, and trying to recover from breaches continues to increase. Regulations about the handling of breaches are being implemented.
Unless your business keeps no records and has no digital transactions, you need to protect yourself. What worked 5 years ago is not enough anymore.
You don’t need to spend a lot of money, but you do need to take security seriously. Enable MFA. Use proper access control. Invest in awareness education for your team. Get the latest best practices for data privacy, strong passwords, and digital hygiene, and follow them.
And let me know if you have any questions. My team and I are happy to help.
“Nearly One Quarter of All Emails are Considered to be Malicious”
That’s a headline on the KnowBe4 blog.
They go on to discuss Fortra’s latest quarterly report from July, Phishing Trends and Tactics: Q1 of 2023.
“The ripple effect from cybercrime-as-a-service launching a few years back has reached critical mass, where we’re seeing significant increases in the percentage of emails that are either clearly determined to be malicious (7.7%) as well as those suspicious enough that users are recommended to not engage with (15.9%).”
Now, this doesn’t mean 1 in 4 emails in your Inbox is malicious. As a client, you have spam filters and a variety of tested tools in place protecting you from known and suspected scam messages.
But some will always get through. And their numbers are increasing. So it is critical that you and your team know how to identify potential threats and handle them without jeopardizing your network.
Creative Criminals – The Latest Tactics
Barbie Scams
Researchers at McAfee report that scammers are taking advantage of the Barbie craze to lure victims.
“As Barbie makes her debut on the big screen, scammers are aiming to cash in on the summer blockbuster,” says Steve Grobman, McAfee’s Chief Technology Officer. “A rash of scams have cropped up online, including bogus downloads of the film that install malware, Barbie-related viruses, and fake videos that point people to free tickets—but lead to links that steal personal info with spyware instead.
Cybercriminals are always on the lookout for opportunities to make scams more attractive and believable. They often leverage popular and well-publicized events such as movie premieres, concerts, or sporting events to trick users into clicking on malicious links.”
Threads App Spoofs
Since Meta launched its Threads app to compete with Twitter, researchers at Veriti have observed hundreds of spoofed domains.
“In recent weeks, we have observed a surge in the creation of suspicious domains, with over 700 domains related to Threads being registered daily,” the researchers write. “These domains pose a significant risk as they can be used to deceive users, distribute malware, and lure unsuspecting individuals into downloading untrusted versions of the app.”
Malicious QR Codes
Computer security service Inky reports a new scam tactic that uses QR codes to trick employees out of their login credentials.
Love them or hate them, QR codes surged in popularity during the pandemic. We all got used to scanning them in restaurants and other businesses, and they haven’t gone away since.
Now Inky has multiple reports of emails that appear to come from within the company and claim to have some sort of issue to resolve such as account verification, 2FA, or password change. The message impersonates Microsoft and includes a QR code that you’re supposed to scan to go to a secure page to fix the issue.
This shouldn’t work. No one should receive an email and then have to use their phone to scan an image to follow a link. The link should simply be included in the email.
However, when we’re rushing, we don’t often think these things through. And this scam is particularly devious because, as Stu Sjouwerman, CEO of KnowBe4 says,
- “I’m not aware of any security solution that can follow a QR code-based URL to determine if the resulting URL is malicious or not.
- It shifts the actual threat action to another device – specifically one that has far less protections than a user’s endpoint.”
.Zip Domains
Researchers at Fortinet warn that cybercriminals are exploiting the introduction of “.ZIP” as a new generic Top-Level Domain (gTLD) to launch email attacks.
“Cybercriminals are always on the lookout for new opportunities and techniques to exploit, and the recent availability of ‘.ZIP’ domains for public purchase has unfortunately created such an opportunity,” the researchers write. “While the pool of new gTLDs has made detection more difficult, adding .ZIP is especially noteworthy given its more common use as a file extension for compressed files.
This new domain extension will likely create confusion, especially among non-technical users, giving [scammers] a new and potentially effective tool to add to their attack arsenals. In [these] campaigns, a common tactic is to make malicious websites appear as legitimate as possible. Using a .ZIP domain can add an air of authenticity to a fraudulent site. A user may mistake the .ZIP in the URL for a file extension, believing they are downloading a file rather than visiting a malicious website.”
On the Horizon
In addition to the scams described above (that you should look out for and share with others), this is one experts expect to see in the near future. It has not been reported yet, but if you’re prepared for it, you’re protected either way.
Google recently announced that they will begin deleting accounts that have been inactive for 2 years or more. The earliest this will start is in December. However, they have begun sending notifications out now.
Experts expect scammers to send their own spoofed notifications to try to steal login credentials. “It’s only a matter of time” they say.
How can you stay safe?
If you have a Google account, you can keep it active through any number of activities including reading an email, watching a YouTube video, using Google Drive, etc.
And if you get any urgent account alert emails, you should examine them carefully. Don’t click on any links in the email, and log into your account independently.